New Study Reveals Insights into Insider Computer Abuse and Organizational Security
July 12, 2023

SDEIS Associate Professor A.J. Burns
Insider computer abuse (ICA), or the unauthorized and deliberate misuse of organizational information resources by insiders, continues to be a significant threat to organizational information systems security. Despite efforts to deter and sanction such behavior, recent studies have shown that many employees are willing to share confidential or regulated information under certain circumstances, and a significant number of security breaches are linked to insiders. These findings indicate that current security measures, mostly relying on deterrence-based sanctions, are not effectively addressing the issue of ICA.
Purpose of the study
Stephenson Department of Entrepreneurship and Information Systems Associate Professor A.J. Burns and co-authors addressed the ongoing issue of ICA in their recent study titled, “Going Beyond Deterrence: A Middle-Range Theory of Motives and Controls for Insider Computer Abuse,” published by Information Systems Research.
In this study, the researchers seek to gain a deeper understanding of insiders' motivations and the controls that influence their behavior. They proposed a middle-range theory of ICA that focuses on the inherent tensions between insider motivations and organizational controls. The researchers identify two categories of personal motives that help explain why insiders might commit ICA: instrumental motives, driven by financial benefits, and expressive motives, driven by perceived psychological contract violations. The theory also examines two classes of controls that help explain why insiders might not commit ICA: internal controls, such as self-control, and external controls, such as organizational deterrence.
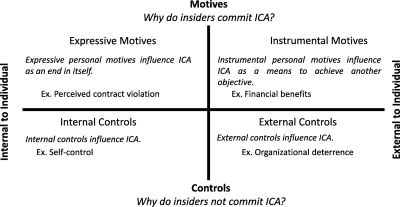
Research Findings
To test their theory, the authors developed a research model and conducted an empirical study involving 532 full-time professionals. The results of the study reveal that both instrumental and expressive motives were found to be positively related to ICA. Additionally, internal self-control had a significant direct effect and also weakened the influence of both instrumental and expressive motives on ICA. On the other hand, organizational deterrence was not directly related to ICA but instead only weakened the influence of the instrumental motive in the study (i.e., financial benefits). In all, these findings show that reducing ICA requires controls that are calibrated to address insiders’ potential expressive and instrumental motives. More specifically, the broad influence of intrinsic controls, such as self-control, highlights the limitations of sanction-based organizational deterrence approaches.
Insights for Practitioners
The implications of this study are significant for both organizations and the public. By understanding the underlying motivations and controls that influence insider behavior, organizations can see that a security program only comprised of sanctions is insufficient. Companies should strive to develop more effective strategies to prevent and mitigate ICA by adopting a broader consideration of insiders' motives beyond deterrence, including the importance of internal controls such as self-control. Organizations can implement measures to promote self-control among employees and improve their security protocols accordingly.
For the public, this study sheds light on the complexities of insider threats and the need for comprehensive security measures. It emphasizes the importance of organizations protecting sensitive information not only from external threats but also from potential abuse by insiders. Individuals can also benefit from understanding the motives behind insider behavior, enabling them to recognize potential warning signs and take appropriate actions to protect their information.
Overall, Burns and his co-authors provide valuable insights into insider computer abuse and its implications for organizational information security. By addressing the tensions between insider motivations and organizational controls, organizations can enhance their security practices by embracing the complementary relationship between behavioral and technical security perspectives to better safeguard their information assets. The findings of this study serve as a foundation for further research and offer practical guidance for organizations seeking to mitigate the risks associated with insider threats.
Read the full study: https://pubsonline.informs.org/doi/10.1287/isre.2022.1133
About the Stephenson Department of Entrepreneurship and Information Systems
The Stephenson Department of Entrepreneurship and Information Systems at LSU’s E. J. Ourso College of Business combines teaching and research to create a rich learning experience for its students. Relationships with industry and state agencies enable the department to assist organizations with issues related to entrepreneurship, information systems, analytics, and business intelligence, as well as innovation and technological change, and offer enhanced career opportunities for its graduates. Collaborative research efforts of its diverse faculty have resulted in major grants from the National Science Foundation and the state of Louisiana.